Looking for “the one” online? Though dating applications and websites present a proper platform to meet potential partners, one should not just throw all caution to the wind, especially against cybercrimes preyed on them. Even dating applications are not spared from the hawkish eyes of hackers. According to the US Federal Bureau of Investigation (FBI), this is the latest scam to prey on those who want to find love through their favorite dating apps.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Fake Verification Processes on the Rise in Dating Apps
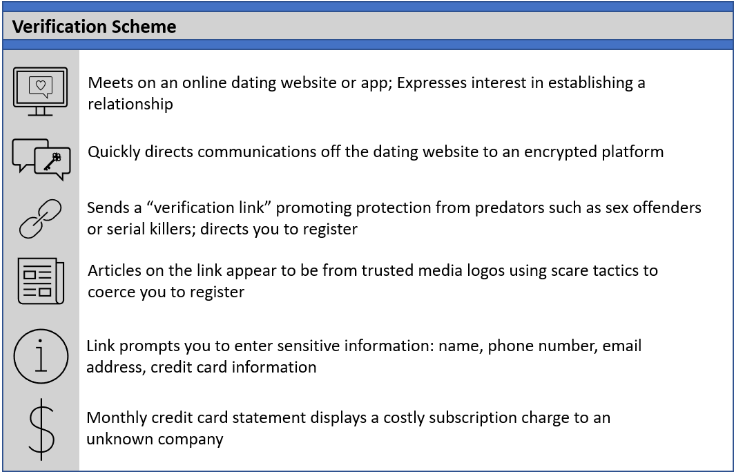
In its recent report, the FBI has disclosed how hackers have come up with faux verification processes that are solely meant to exploit the willingness of individuals who want safe connections online. These are all misleading measures under the guise of real security features. They just persuade the user with the promise of a safer dating experience and later phishing personal information, credit card details, or both from him.
Hackers have implemented exploitative ways of preying on the desire for safety and security in online dating to rope unsuspecting members into a paid membership. The FBI has explained the process of the new verification scam on dating sites to the public. Here’s how it unfolds:
Build a Connection: You start a fun conversation with an interesting person on some dating platform. The person can even seem real and open to connecting, taking conversations off the app or the site quickly onto private messengers or texting.
The Trust Factor: Under the clothes of safety and some trust-building environment, a scam sends you a link to some website, supposedly with the advertisement of “free” verification. Supposedly, the “verification” saves one from fake profiles or, even worse, dangerous people.
The website even goes on to authenticate the genuineness of its site through phony articles and testimonials.
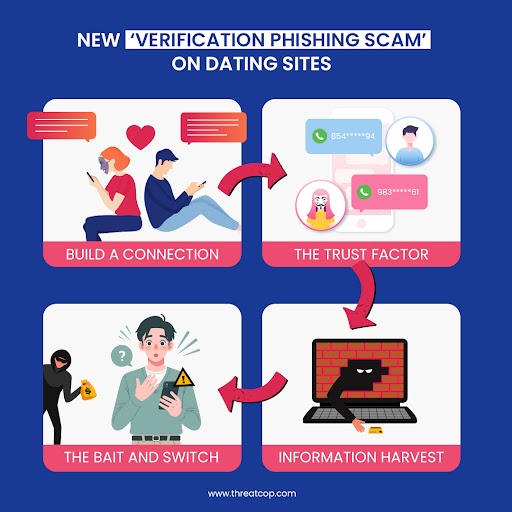
Information Harvest: To fill in the “verification,” you are asked to fill in personal information like your name, phone number, email address, and most alarmingly, your credit card number.
The Bait and Switch: On entering your details and information, you get automatically registered to a dating website with poor services, with monthly subscription charges that will be drawn from your account.
Book a Free Demo Call with Our People Security Expert
Enter your details
Let’s understand it with an example:
So let’s say you are on a dating app, and by some chance, you get matched with a certain girl, “Sarah.” She looked all sweet and good, as they all do. Not a few moments later, she’s already requesting the conversation be moved over to a texting app for “privacy.” A little while later, mentioning something about a “free verification process” so nobody gets hurt, she sends a web link.
This site looks real but is full of fake articles on online safety. It does ask for your name, phone, email—everything—even your credit card number to ‘verify’ you. Believing it’s legit, you, of course, fill in your details.
There’s a spin to this; you’re not verified. Instead, you’ll unwittingly be signed up for some substandard dating website with hidden monthly fees that companies only charge to people who fill in their real details on their website, and then your credit card gets charged monthly by some company you haven’t even heard of. And all your information, including your name, phone number, and credit card information, is at risk of getting stolen for identity theft, or even worse, sold on the dark web.
Sarah was looking not for love but for your money and information.
How to Avoid Verification Scams
Searching for love on an online dating site should never be done in exchange for putting your security at risk. The following are ways by which you can safeguard yourself from being duped by these verification scams:
- Dont click on Unfamiliar Links
- Stay on the same dating platform
- Free Verification is a Myth
- Research the dating site before you sign in
- Do not share personal information that quickly
- Video chat before meeting up
- Meet in a public place
If you find some fishy link on dating sites or through someone, report this request to the dating site and the FBI through their Internet Crime Complaint Center (IC3). Report the attempt on fraud with IC3: https://www.ic3.gov/.
Also Read: Benefits and Purpose of Security Awareness Training
People Security Culture is the need of the hour
Just like online dating, navigating the digital world requires a healthy dose of doubtfulness and a reliance on your instincts. But this vigilance extends far beyond dating sites. Phishing attacks, ransomware, and data breaches are just some of the ever-present threats organizations face. To combat these threats, fostering a strong people security culture through cybersecurity awareness training is critical. A strong people security culture, built on cybersecurity awareness training, is essential for protecting your employees from a wide range of threats. To combat cyberattacks, organizations implement security awareness training (SAT). At Threatcop, we provide organizations with TSAT (Threatcop security awareness training) to make their employees the first line of defense. Here’s how TSAT empowers employees to combat scams:
- Identifying Red Flags: Training equips employees to recognize common tactics used by scammers, such as phishing emails, fake profiles, and pressure to share personal information.
- Verifying Information: Employees will understand the importance of verifying information online.
- Protecting Sensitive Information: Training emphasizes the importance of safeguarding sensitive data like passwords, credit card numbers, and social security numbers.
- Reporting Suspicious Activity: A strong security culture encourages open communication. Employees should feel comfortable reporting suspicious activity to IT or security teams to investigate further.
Building a strong people security culture is an ongoing process. Know more about TSAT by getting in touch with our team and prioritizing awareness to create a safer digital environment for everyone in your organization.
Read our People Security Guide to learn more about people security culture

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
