Email is the playground for cybercriminals and Business Email Compromise (BEC) is still the top threat. According to the FBI’s Internet Crime Complaint Center (IC3), BEC attacks accounted for over $4.3 billion in losses reported to the agency in 2023. This staggering figure highlights the continued dominance of BEC scams as a major cyber threat. This blog post draws insights from new research by Kroll which explores the prevalence of BEC attacks.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is a BEC Attack and How Does it Work?
Business Email Compromise (BEC) is a sneaky cybercrime where attackers pretend to be someone you trust within your organization to get you to send money or sensitive info. Imagine a scammer posing as your CEO asking for an urgent wire transfer to a new vendor – that’s BEC.
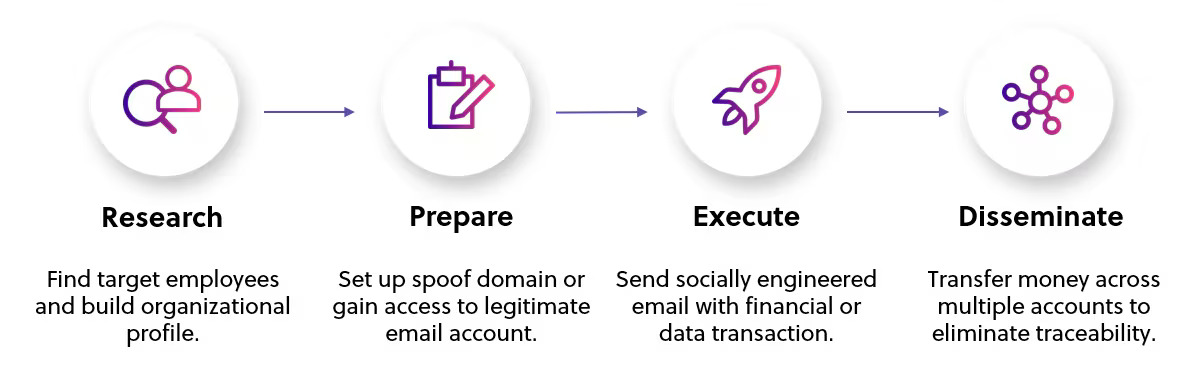
Here’s how BEC attacks work:
- Reconnaissance: Attackers gather info about your organization through social media or data breaches.
- Impersonation: They spoof the email of someone you trust, like a CEO, colleague or vendor.
- Urgency & Deception: The email creates urgency or leverages a trusted relationship to get you to take action. This could be an urgent wire transfer, change to payment instructions for an existing vendor, or sharing of sensitive data.
- Financial Gain: The victim believes the email is legit and sends money or info directly to the attacker.
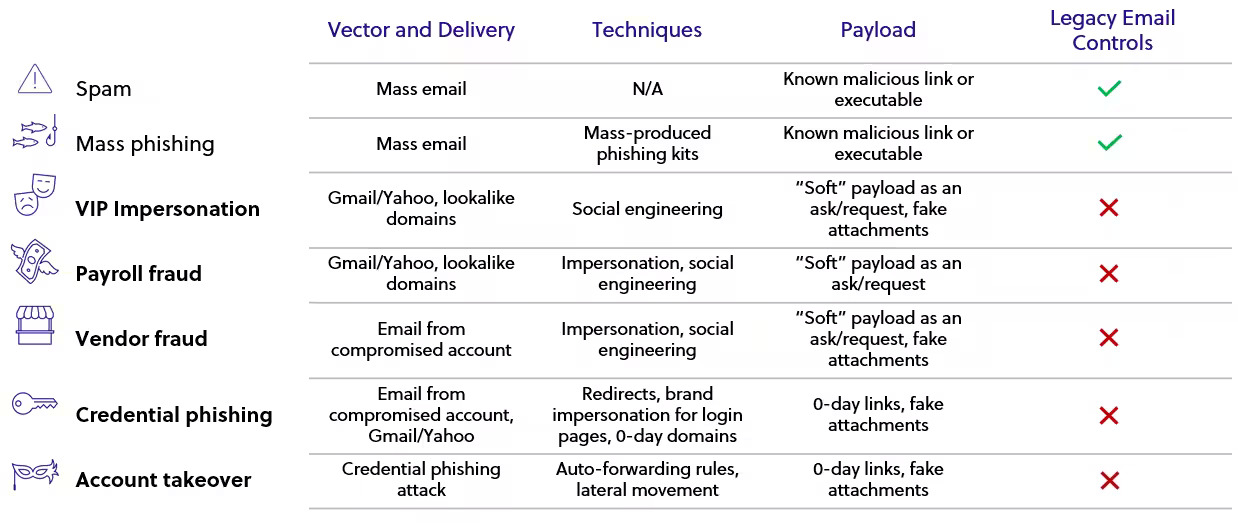
Types of BEC Attacks:
- CEO Fraud: Attackers pretend to be the CEO and email finance department employees to request wire transfers or changes to payment terms for existing vendors.
- Vendor Email Fraud: Attackers pretend to be a vendor and email accounts payable to pay fake invoices or change payment details for existing vendors.
- Account Takeover (ATO) Fraud: Attackers compromise a company email account and use it to launch BEC attacks from inside the organization. This could be an employee, vendor, or client account.
- Attorney Impersonation: Attackers pretend to be a lawyer or attorney working with the company and target HR or legal to request employee data or wire transfers.
- W-2 Email Phishing: This scam targets employees during tax season. Attackers pretend to be HR or the payroll company and ask employees to update W-2 tax forms, and employees give up their Social Security numbers.
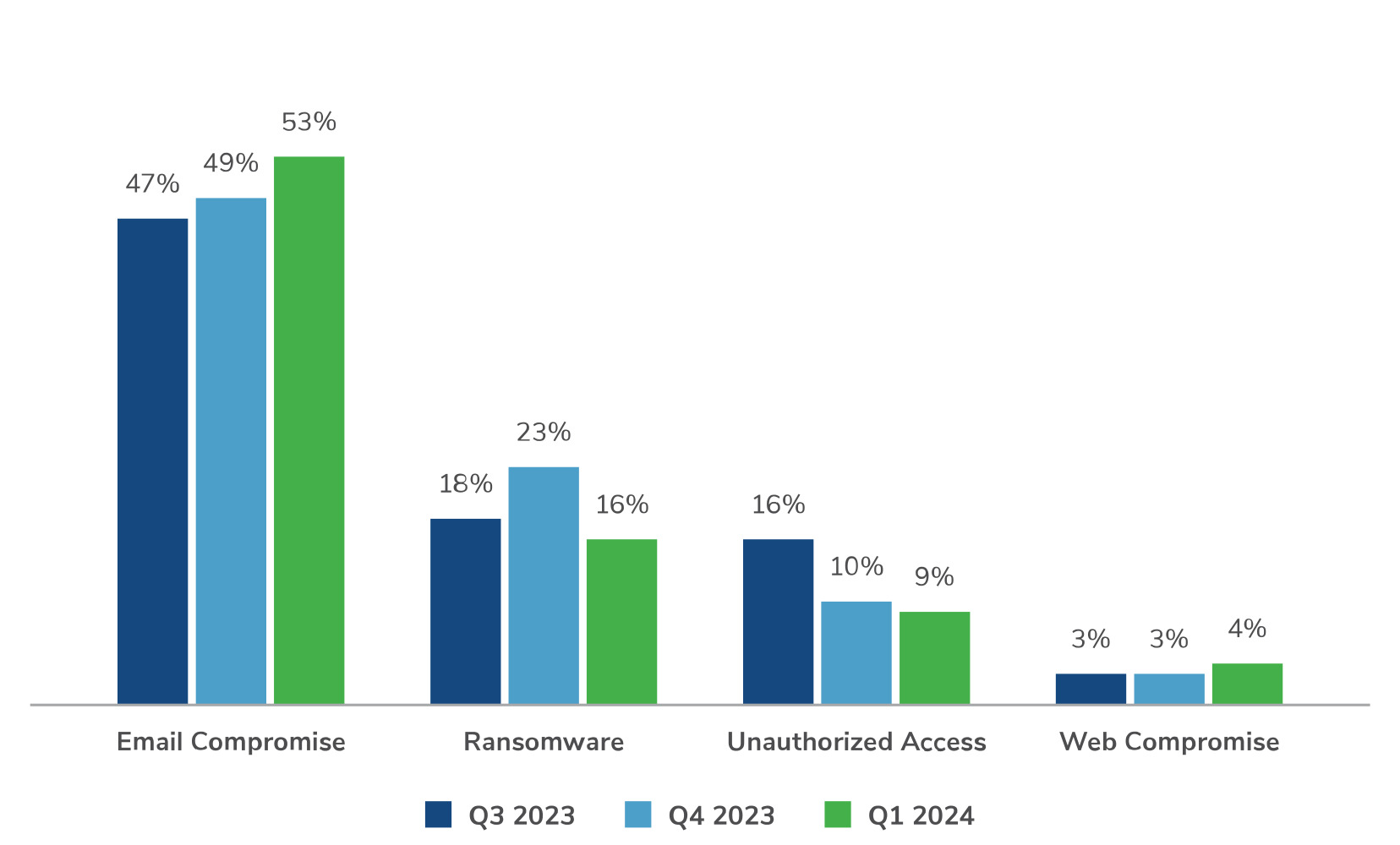
Email Compromise Continues to Dominate as Top Threat
Kroll’s Q1 2024 Cyber Threat Landscape Report paints a concerning picture: email compromise attacks are steadily increasing. Their data, spanning the past three quarters, reveals a consistent upward trend in this malicious activity.
This research goes beyond just identifying the rise of email compromise. Kroll’s commentary sheds light on the evolving tactics of attackers. They highlight the shift beyond traditional email phishing, noting an increase in the popularity of methods like “SMS lures” and “voice phishing” (vishing). This aligns with observations of increasing smishing attacks, further validating Kroll’s insights into the current threat landscape.
Kroll’s research serves as a wake-up call for organizations. The evolving tactics employed by attackers signify their constant evaluation of what works and what doesn’t. They adapt their methods to maximize the chances of compromising an email account.
However, Kroll leaves us with hope. Their research emphasizes the critical role of security awareness training. By educating users to be vigilant and identify suspicious attempts to steal credentials, organizations can significantly reduce the risk of falling victim to these attacks.
Why Hackers Succeed and How to Stop Them
Email compromise attacks succeed because of one thing: human error. Hackers target users who aren’t paying attention and unwittingly give up their credentials. That’s where security awareness training comes in as a hero.
Understanding the Vulnerability:
Think of a hacker as a magician. Their trickery relies on misdirection and exploiting your blind spots. In the digital world, those blind spots are users who miss red flags in an email or overlook suspicious bits. A well-crafted phishing email can look legit, especially when it uses urgency or impersonation.
The Power of Awareness
This is where security awareness training comes in. By training employees, you turn them into cybersecurity detectives. Training teaches them to look out for the telltale signs of phishing, including:
- Spoofed senders: Is the email from someone you know, but the address is slightly different?
- Urgency tricks: Is the email asking you to act now without verification?
- Weird attachments or links: Are you being asked to click a link or download an attachment from someone you don’t know?
How Threatcop DMARC Can Help to Stop BEC Attacks?
Protecting your business from BEC attacks requires a layered approach. Threatcop DMARC (TDMARC) is the solution. It gives you email authentication, domain monitoring, and anti-spoofing. That means blocking company impersonation, supplier impersonation, lookalike domains, domain spoofing, display name spoofing, and even supplier impersonation domains.
Securing Your Business with Threatcop DMARC
Threatcop DMARC (TDMARC) is a powerful tool that helps you:
- Spot Fake Emails: It identifies emails that try to impersonate your company or your suppliers.
- Stop Spoofing: It makes it much harder for scammers to spoof your email address or domain name.
- Stay Compliant: It ensures your email authentication is set up according to industry standards (SPF, DKIM, and DMARC).
Benefits of TDMARC
- See Who’s Risky: Identify suppliers most likely to be impersonated in an attack.
- Deep Email Analysis: Analyze various aspects of emails, like sender IP, location, and even the content of the message.
- Find Fake Websites: Uncover websites designed to look like yours or your partners’.
- Control Your Display Name: Choose how email senders using your domain appear in inboxes.
- Easy BIMI Setup: Simplify the creation and validation of BIMI records, which helps display your company logo next to your emails in some inboxes.
TDMARC keeps you compliant with email authentication standards (SPF, DKIM, DMARC) and gives you visibility. It shows you high-risk suppliers, analyzes email content for malicious intent and finds fake websites that trick employees. With TDMARC, you can also control how email senders using your domain look.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
