Think your inbox is secure? Think again. Threat actors are constantly developing new methods and are now using a fairly high level of sophistication that cuts through even the toughest defense mechanisms. The Verizon Data Breach Investigations Report 2023 notes that even up to that year, emails still stand out as the main cause of data breaches, with 56% of the attacks escaping outdated security filters, according to ArmorBlox. The figures say it all: email security is no longer an option but has become a must-have.
Table of Contents
ToggleHackers come armed with a multi-stage attack chain aimed at your defenses. This includes phishing scams and business email compromise (BEC) amongst the arsenal of weapons they use to infiltrate your systems—from malware attachments to innocent-looking QR codes. It naturally leans toward neutralizing the threat long before it even gets to your inbox.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
But inevitably, some emails will go through your system. Harden your email security, and you may need something more than basic filtering and strong protection after delivery.
Read More: Email Impersonation Attacks Are on the Rise
Phishing emails easily bypass traditional security for many reasons:
Social engineering:
Emails of an emotional, time, or trust pressure type that induces a user to click on a harmful link or open an attachment.
Example: Subject: Urgent! Your account has been suspended!
Body: We noticed suspicious activity on your Netflix account. Click here to verify your identity and avoid account closure: [MALICIOUS LINK].
Spoofing:
Phishers can easily mask sender addresses to appear as if they are being sent from legitimate sources, making it hard to distinguish them from real emails.
Example: From: www.Micros0ft.com
Subject: Important Security Alert from Your Bank
Body: Dear [Your Name], Our records indicate unusual activity on your bank account. Please verify your information by logging in through this secure link: [FAKE BANK WEBSITE LINK] to avoid any restrictions.
Human error:
Even the most vigilant user can be duped by the subtle disguising of malicious content. Phishing emails focus on human frailties, easily escaping filters that pay attention to only technical aspects.
Example: Subject: RE: RE: RE: Important Document – Action Required
Body: This is a reminder that your tax documents are expiring soon. Download but also now before they are inaccessible: [MALICIOUS ATTACHMENT].
Book a Free Demo Call with Our People Security Expert
Enter your details
Limitations of Traditional Phishing Response in Email
While user reporting and manual analysis are common approaches to dealing with emails that land in inboxes, they have limitations:
- Delayed Response: Identifying and remediating threats can be slow, leaving organizations vulnerable for extended periods.
- Limited Employee Involvement: Employees aren’t actively involved in identifying phishing attempts. This can be slow and leaves vulnerabilities undetected.
TPIR: Single-click Email Reporting and Incident Response
Threatcop Phishing Incident Response (TPIR) is the most updated service in cloud-based email protection. This tool is not only for reaction but also for giving your employees the possibility of being part of their security plans through a single-click email reporting button. Incident Response is a key way to understand and react to phishing attacks, which will help an organization increase its resilience against credential theft, malware infection, and business disruption. This is how TPIR enables one organization to take control in response to a phishing incident:
- Employee-powered threat detection: Employees can easily report an email from their inbox that they believe could be a phishing activity with just one click.
- Automated threat recognition: It not only scans URLs and attachments but also verifies the sender’s email security protocols, like DMARC, SPF, and DKIM.
- SOC Team Incident Response: It helps the SOC team quickly identify and remove the phishing activity from the entire organization.
Know More About TPIR Here
How does TPIR help prevent BEC attacks?
Its easy-to-use, single-click reporting system allows employees to flag suspicious emails. This further helps the SOC team identify and quarantine any potential phishing from the entire organization:
Enhanced Security for Attachments and URLs/Links:
Phishing emails often exploit employees by clicking malicious links or downloading infected attachments. TPIR combats these threats with a multi-pronged approach:
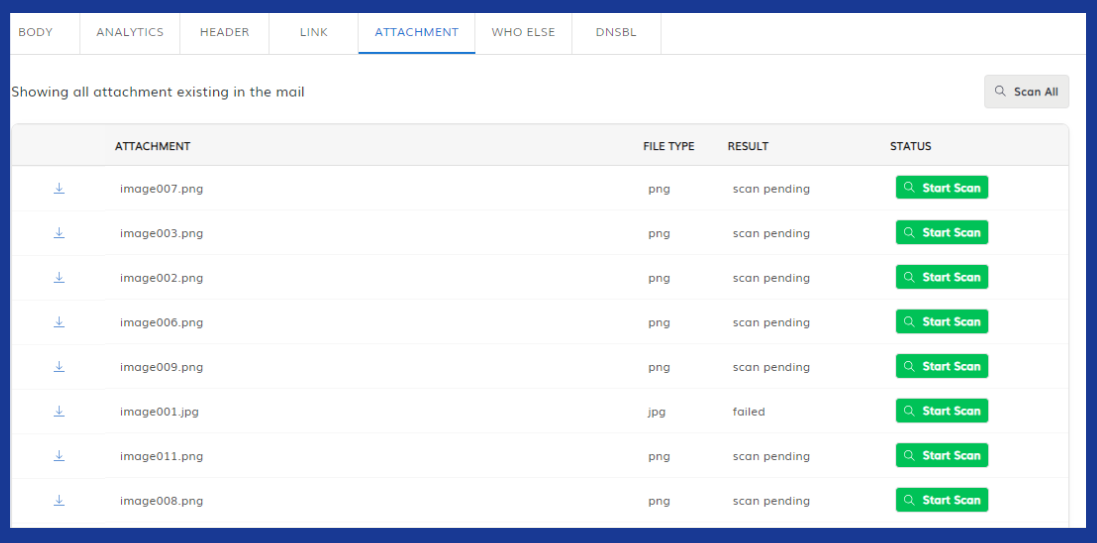
1. Threat Intelligence Analysis: TPIR utilizes threat analysis to identify malware.
Here’s how it works:
- Every file has a unique digital fingerprint called a hash. TPIR possesses a vast database of hashes associated with known malware.
- When an email arrives, TPIR calculates the hash of any attachments.
- If the attachment’s hash matches a hash in the malware database, TPIR flags the email as malicious (as indicated by the “Start Scan” status next to “image001.jpg” in the image, which could be a potential malware hit).
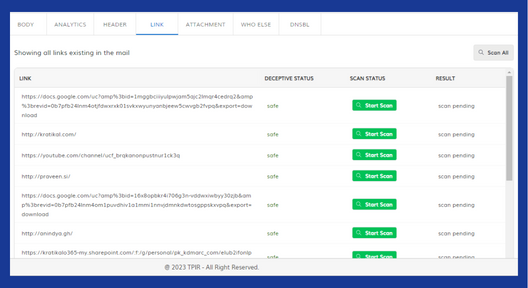
2. URL Link Analysis: TPIR analyzes URLs within emails to identify suspicious links. If a URL matches a known phishing site or exhibits other red flags, TPIR can flag the email as malicious (indicated by the “Start Scan” status next to “http://kratikal.com” in the image, which could be a potential phishing link).
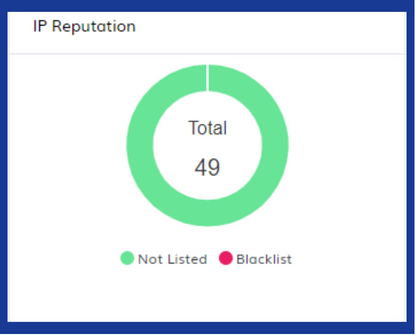
IP Reputation Check:
TPIR checks the sender’s IP address against global blacklists of known malicious sources. A bad reputation score raises a red flag.
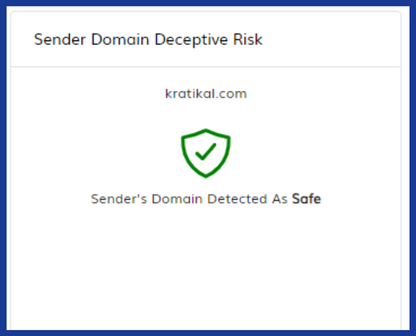
Deceptive Domain Verification:
TPIR goes further than just making sure the sender’s email address is valid. It verifies the domain name for possible misspellings, weird characters, and even a subdomain pretending to be from an actual company.
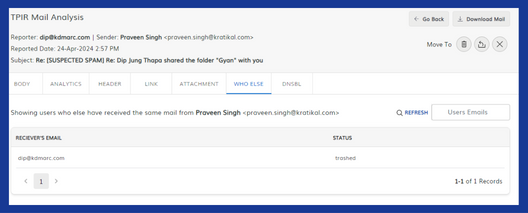
“Who Else” Reporter Insights:
TPIR utilizes the collective experience of your organization. If a similar email has been reported by several users, this will increase the priority of the investigation. Realize, though, that most large-scale phishing campaigns usually carry higher urgency.
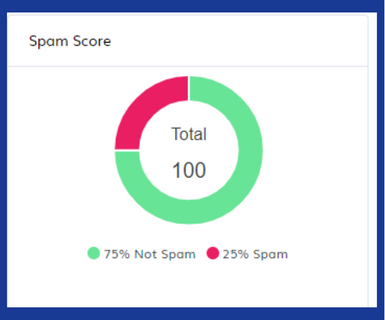
Spam Score:
TPIR checks for many things, all the way from the reputation, sender’s keywords, and formatting to known spam indicators, to give a ‘spam score’. If it passes this limit, the email is marked for review.
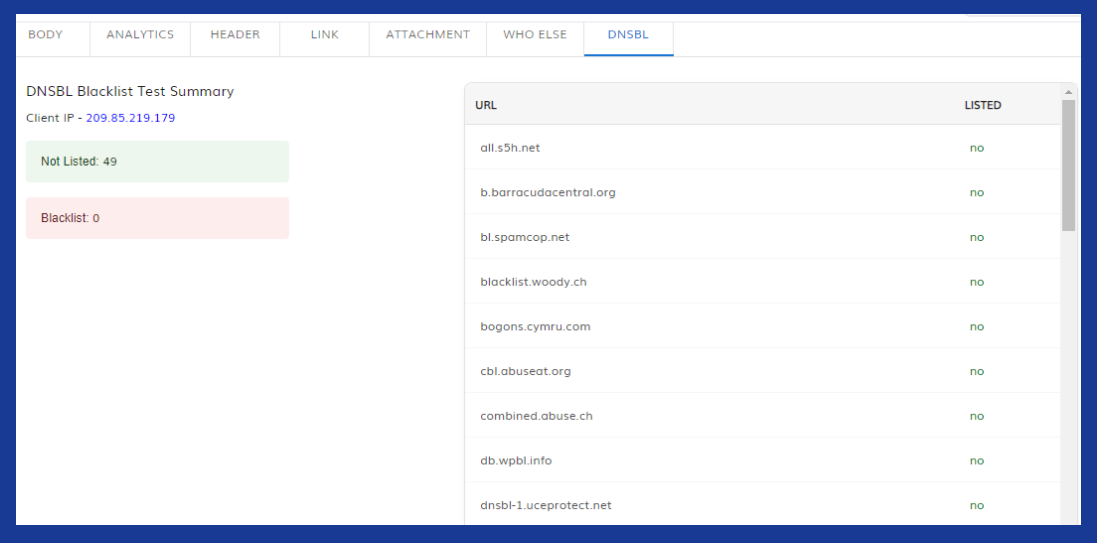
Database of a global threat record:
TPIR is linked with a well-updated database of bad URLs, domains, and email addresses. Thus, TPIR does have access to such real-time intelligence that it would detect the newest tricks for phishing.
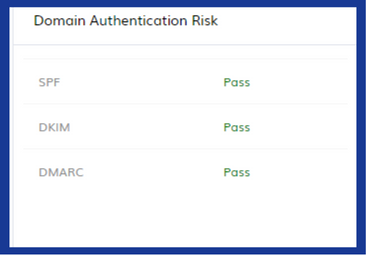
Successful SPF, DKIM, and DMARC Verification:
TPIR validates these email authentication protocols to ensure the sender’s identity is legitimate. Inconsistencies or failures can indicate email spoofing attempts.
User-Reported Analytics:
TPIR analyzes user-reported emails to identify trends and patterns. This helps security teams understand your organization’s specific vulnerabilities and tailor future training programs to address them.
Key advantages of implementing TPIR
The implementation of Threatcop Phishing Incident Response helps system administrators not only streamline the process of email threat management but also enhance the overall organizational security framework. Here are some ways it transforms your security landscape:
1. Streamlined Threat Management Interface:
It provides a central, intuitive control panel that simplifies the tracking and management of email threats, from initial detection to resolution.
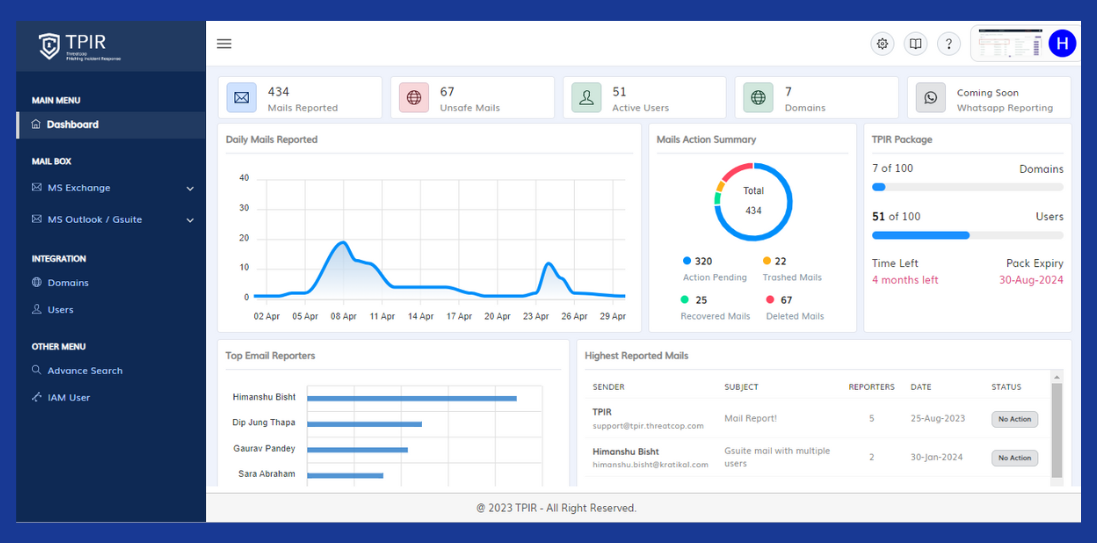
2. Speed up Incident Response:
Modern technology can quickly identify and therefore neutralize email threats, thus improving the organization’s speed in responding.
3. Minimal Infrastructure Requirements:
Being a cloud email protection solution, TPIR simplifies deployment and ongoing maintenance without the need for extensive on-site hardware.
4. Enhanced Operational Efficiency:
Eases integration with already existent security frameworks, resulting in smoother management and an improvement in operational efficiency.
5. Increased Proactive Threat Detection:
Increases the capability to identify new and emerging threats early, even at a proactive stage, and to counter them by developing deep insights into the dynamics of threats and user behavior.
6. Communication automation to inform
Automates reminders to ensure that all stakeholders know the status of all threats promptly and timely.
7. Optimization of Security Resources:
This is yet another way to automate monotonous security tasks to free up the security team to spend more time on strategic initiatives and more complex troubleshooting.
Mitigate Email-based Attacks
The automated incident response does not only cater to phishing defenses; the measure gives tools to both security personnel and employees for an active email protection strategy. This proactive approach helps dismantle the attack chain at multiple levels to provide strong protection against sophisticated email threats.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
