
For quite some time now, iNSYNQ was under the scrutinizing eyes of various social network platforms as well as on web hosting review sites due to its lack of updates. The servers of iNSYNQ were locked with ransomware outbreaks. Spammers rooted around the internal network of the company prior to the deployment of the Ransomware for a period of ten days.
Table of Contents
ToggleThis ransomware outbreak hit QuickBooks cloud hosting firm iNSYNQ during the mid of July. It is a cloud computing that is a provider of virtual desktop environments. The attack rendered the cloud hosting firm’s customers’ files inaccessible because of the ransomware attack. The attack appears to have started with an email phishing attack. The attack was successful as it hit employees working in the sales department for the company.
What is the Company’s Take on It?
The malware encrypted some iNSYNQ customer files, most of these were smaller files and did not include QuickBooks or Sage files. The malware has also spread into some of the backups. If the company turned on the backups, there was a good chance that the virus would then start to spread across the entire network through the backup system. So, the company treated the backups similarly to how they were treating the primary systems.
Many of iNSYNQ’s customers are accountants and when the company took its network offline on July 16 in response to a ransomware outbreak. Some of its customers took to social media to complain that iNSYNQ was not answering them. In view of the damage caused by the ransomware attack, the company has decided to offer its customers a two-month credit.
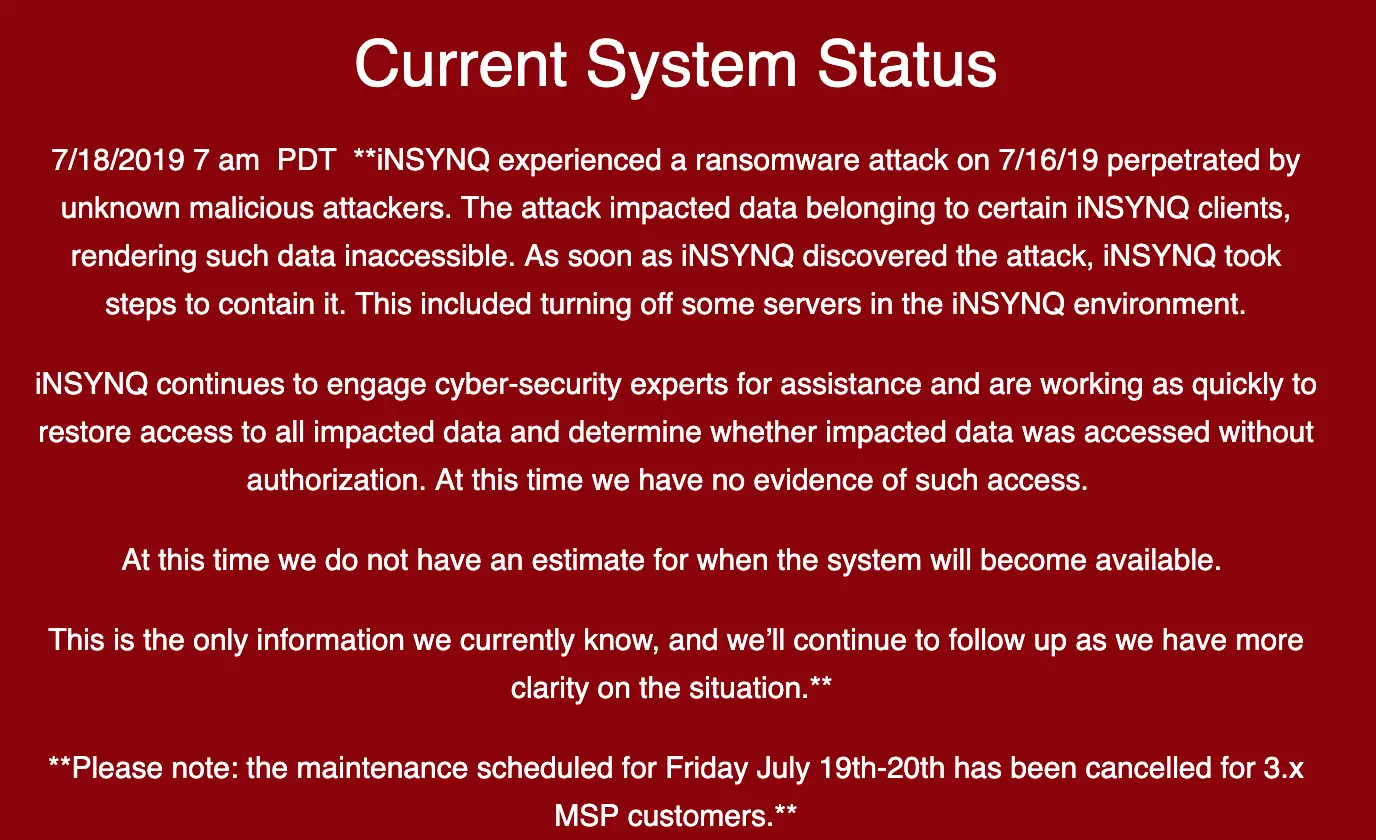
The company is investigating the attack, however, no evidence has been found that the customer data has been accessed. The ransomware attack’s time-consuming recovery steps are incompatible with the always-on business-like “web hosting”.
The attackers left a ransom note which states that:
“We are working for profit. The core of this criminal business is to give back your valuable data in the original form (for ransom of course)”
As per the company, the ransom was a very substantial amount and had the money wired to pay it in cryptocurrency. They were able to contain the encryption part of up to roughly 50% of customer systems.
What Does This Situation Tell Us?
The ransomware attack was successfully initiated through a phishing email that was deployed on an employee in the sales department. It is, therefore, evident that even a single victim employee can cause havoc within the organization. He might become responsible for bringing the organization in ruins.
Book a Free Demo Call with Our People Security Expert
Enter your details
It is, thus, important to ensure that employees within an organization are aware of the probable cyber threats that can threaten the entire cyber infrastructure.
What Could Have Been Done?
- Regular overview of all the devices that are connected to the organization’s network and the permissions granted to these devices.
- Configure access controls including directory, files, and network share permissions with the least privilege. Not every user should have access to these files, directories, or shares.
- Use application whitelisting that will only allow systems to execute programs that are known and are permitted by the security policy.
- Implement Software Restriction Policies (SRP) and other controls. These will help to prevent the execution of programs from common ransomware locations. This includes temporary folders, supporting popular Internet browsers or compression/decompression programs including the LocalAppData/ AppData folder.
- With a cybersecurity attack simulator and awareness tool, TSAT, employees not only face dummy cyber attack but also, inculcate a sense of awareness against various attack tactics. This is done with customized learning-based modules and assessments. This process helps in increasing employees’ immunity toward cyber attacks.
