Identify the current email threats that are targeting organizations in Qatar!
Table of Contents
ToggleToday almost every company uses email as a primary communication channel in Qatar or around the world.
However, email is also often used by cybercriminals to spread malware or steal personal information. Sometimes these emails are so well-tailored that even IT professionals can fall for the trap. Therefore, using email is not safe anymore until and unless one implements the email security measures and protocols.
According to Zawya, more than 4.7 million (4,712,649) email threats were detected and blocked across Qatar in 2020.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
But how do you enforce email security policies when you are not aware of the threat?
That will be like going on a battlefield not knowing who you are fighting against. If you want to win, you need to know the enemy to figure out what tactics you should use.
So, what are the current email threats that are targeting organizations in Qatar?
Phishing
Phishing is a type of social engineering attack often used by cybercriminals to steal personal information. Malicious actors deliver phishing campaigns through email, instant messages, or text messages.
These emails or text messages are stuffed in with malicious links that threat actors trick the recipients to click into. Furthermore, when the recipients click the link they are either redirected to a phishing page or download malware/virus.
According to Qatar Tribune, Qatar is witnessing an increasing number of phishing attacks. The nation witnessed 128,356 phishing attacks in the second quarter of 2020.
“Social engineering scams are a particular concern. With these scams, attackers present a post intended to get the target user to click on a link. That link usually leads to the user downloading some malicious code that has the potential to steal information on the user’s computer or mobile device. These scams are sometimes also called phishing and baiting, as well as click-jacking. Whatever they’re called, just know that not every post on social media is safe to click on. You should take special care to treat every link with suspicion, especially those that look like click bait” – Rick Delgado
BEC Attacks
BEC attacks are another form of email attack. In BEC attacks, the malicious actors impersonate senior officials from an organization such as the CEO or the company’s supervisors. They can also impersonate the organization’s partners to trick the employees and customers into providing their personal information.
Book a Free Demo Call with Our People Security Expert
Enter your details
According to the Gulf Times, BEC attack detections in Qatar increased by 18% from the second half of 2019.
“Qatar and the GCC having high rates of cyber-attacks shows that while the pandemic has dominated all of our lives during the first half of 2020, it’s not slowing down the cybercriminals,” said Assad Arabi, country manager (Qatar) of a cyber security firm.
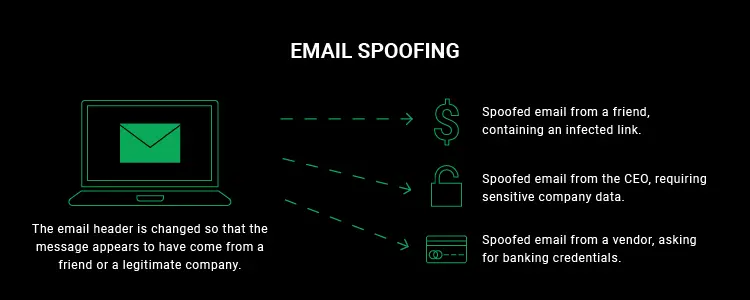
Spoofing Attacks
A spoofing attack is a type of cyber attack where malicious actors impersonate a brand or an individual to trick the recipient. The success rate of spoofing attacks is usually high because here the attackers take the advantage of the trusted relationships between the recipient and the brand or person impersonated.
How to Block Email Threats
Now the million-dollar question arises, How do we block these email threats?
I would say the only and the best solution to prevent email threats is to combine the ability of humans and technology. But this is achievable only when the employees are well aware of the email threats and know how to avoid them. Moreover, the organization is implementing every best cybersecurity measure.
So, how can an organization start with this process?
The first thing an organization can do is to educate the employees about the latest and most common email threats. Providing them with cybersecurity awareness and training will help them gain knowledge of what these email threats look like. Moreover, it will also give them the experience to understand how these threats work and it will also help them in learning how to avoid such email threats.
The next would be to secure the email domain. As mentioned above, most of these email threats are successful because the hackers impersonate a legitimate email domain or brand. However, if organizations stop them from doing so, it will make it more difficult for them to convince the recipients to click the malicious link or download the virus attachment.
Email is the most common cyber threat that exists today. Therefore, deploying the best cyber security measures to prevent email threats is the need of the hour.
Some additional tips:
- Do not click on the link in an email unless you are sure enough it is safe
- Always hover over the link to find the destination of the link in an email
- Create a strong and unique password, also make sure to change the password periodically
- Enforce multi-factor authentication for your email account to add extra security
- Never send your personal information over the email unless you can verify if the sender is legitimate
