As a Security Awareness Leader or CISO, you’ve meticulously crafted a security awareness campaign for your employees, confident it will strengthen your organization’s defenses. But here is the main question– are you truly reaching the most vulnerable individuals? You don’t know what are the chances of each employee getting phished? Without effective data and analytics, you’re essentially flying blind. You lack the crucial insights needed to identify high-risk employees, assess phishing susceptibility rates, and measure the overall effectiveness of your training efforts. Launching endless campaigns becomes a numbers game, not a strategic approach.
This blog cuts through the noise. We’ll delve into the powerful metrics that will empower you as a CISO and security leader to transform your security awareness program. Get ready to make data-driven decisions that equip your organization’s cyber defenses, one informed action at a time. Let’s jump in and discover the key analytics that elevate security awareness from a necessary chore to a strategic advantage. I will also tell you which tool can help you to get all of the above data in one place.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What Analytics Should Power Your Security Awareness Training?
The true power of security awareness training lies not just in educating your workforce, but in understanding its impact. Actionable analytics provide the insights you need to refine your approach and maximize its effectiveness. Here are some key metrics that should be tracked in a good security awareness training tool:
- Assessing Overall Risk: Effective tools offer analytics that measure the average susceptibility of your employees to cyber threats over time. This “risk propensity trend” provides a valuable view of your organization’s cybersecurity posture.
- Identifying Individual Vulnerabilities: Just like fingerprints, employee cybersecurity awareness is unique. Detailed analytics about each employee is essential to identify individuals more susceptible to phishing attempts or social engineering tactics. These insights allow for targeted training interventions, ensuring everyone receives the support they need.
- Campaign Performance Comparison: Did your latest campaign deliver better results than the previous one? Effective analytics offer comparative reports that highlight improvements and areas for further focus. This data-driven approach allows you to refine your training program for greater impact continuously.
- Spotting Repeat Offenders: Some employees might require additional guidance. Tracking the number of users who fall for simulated phishing attacks repeatedly allows you to identify these individuals and provide focused training to enhance their ability to detect real-world threats.
- Reaction Time Matters: The speed of response is crucial in mitigating cyber threats. Analytics that measure the average time employees take to identify and report suspicious activity provide valuable insights into your organization’s overall vigilance. This allows you to identify areas where employees might need additional training on recognizing and reporting phishing attempts.
Data is king in measuring the success of security awareness training programs. Like any investment, you must know if your training is worth the time and effort. This is where data comes in. It tells you how well users learn, and keep knowledge, and if the program works. CISOs and leaders can use data to make smart choices about security.
People Security Made Easy Through TSAT’s Data-Driven Dashboards
The metrics outlined above paint a clear picture: actionable data is the cornerstone of successful security awareness training. But what if extracting these insights was a cumbersome task, buried within a complex interface? Fortunately, there’s a solution that empowers you with both a user-friendly experience and robust analytics – Threatcop Security Awareness Training, or TSAT.
Its intuitive dashboard provides a centralized hub, offering a clear and comprehensive view of your security awareness training program’s effectiveness. Gone are the days of sifting through mountains of data – with TSAT, you have the critical insights you need at your fingertips.
The following are the most specific features of TSAT that cover all the aspects of metrics we discussed above in the blog. It empowers you to harness the power of data and transform your security awareness program.
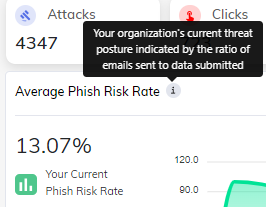
- Phish Risk Rate
- Breach Time
- Completion Rates: Tracking how many employees complete training modules provides insight into overall program engagement. Low completion rates might indicate a need to revamp training content or delivery methods.
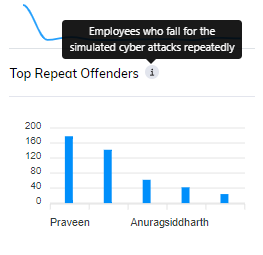
- Top Repeat Offenders: The security awareness tool should take analytics a step further by identifying Top Repeat Offenders. This metric highlights users who consistently fall victim to phishing simulations. By focusing on these individuals, organizations can provide tailored training and support to significantly improve their ability to detect and avoid real-world phishing attempts.
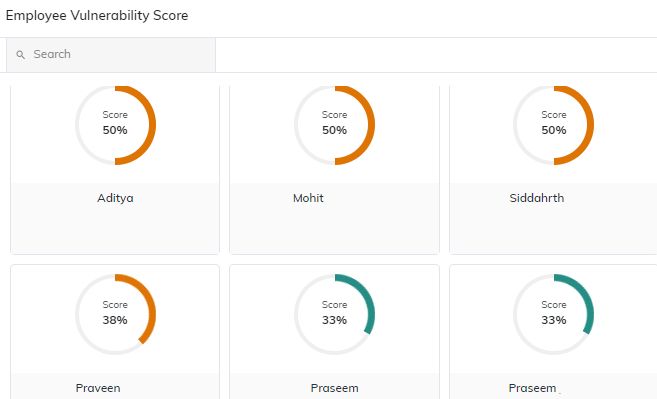
- EVS (Employee Vulnerability Score): This feature provides a personalized risk assessment for each employee. This score identifies their susceptibility to phishing attacks, allowing for targeted training and support to address specific vulnerabilities.
Beyond these core metrics, additional analytics can offer valuable insights. Threatcop provides a tool named TSAT which tracks user progress throughout the training journey. It identifies knowledge gaps and allows for personalized learning paths. These analytics not only demonstrate the ROI of your security awareness training program but also empower data-driven decision-making.
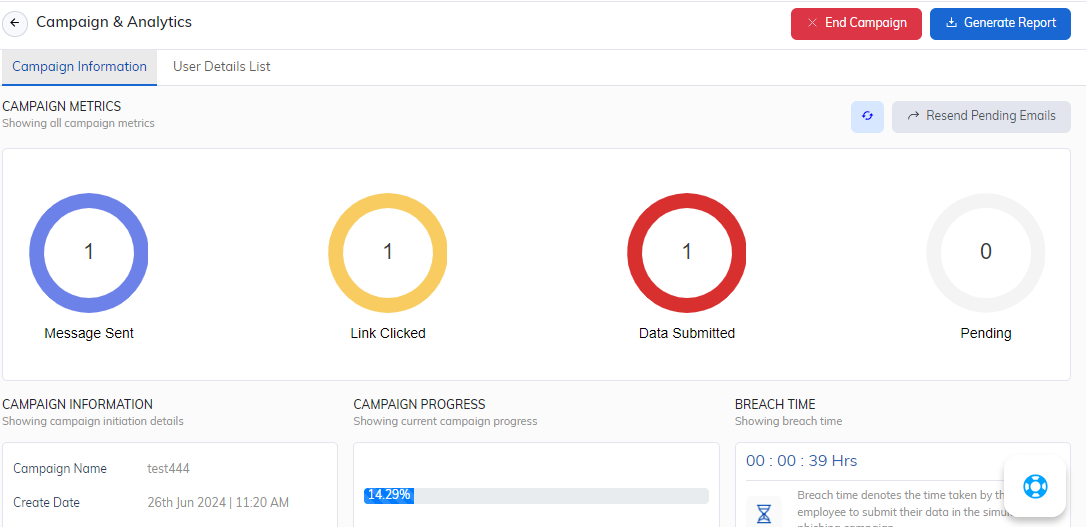
Beyond these core metrics, additional analytics that TSAT provides can offer valuable insights. TSAT tracks your employees’ progress throughout the training journey. It identifies knowledge gaps and allows for personalized learning paths. These analytics not only demonstrate the ROI of your security awareness training program but also empower data-driven decision-making.
The Key Takeaway
TSAT goes beyond just presenting data – it empowers action. These insights are then translated into actionable reports and visualizations, allowing for targeted training interventions and continuous program improvement.
Now you’ve seen the power of data-driven insights in action. Don’t settle for outdated training methods that leave you in the dark. Experience the TSAT difference. Reach out to our Threatcop sales team at [email protected] today to book a demo call and discover how TSAT can transform your security awareness program and fortify your organization’s cyber defenses.
Take a look at Threatcop’s People Security Guide Launched at DSCI AISS 2023

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
