It was in 1834 that the world’s first cybercrime took place. Two brothers used the insider contacts of the French telegraph to steal the financial market’s data. Despite the contemporary image of hackers in hoodies creating havoc at an alarming rate, cybercrimes are nothing new. The only difference between the earlier and present crimes remains the speed and scale at which the attacks happen. According to Cybersecurity Ventures, the cost of cybercrime will increase by 15% annually over the following years, reaching $10.5 trillion by 2025. It is not even surprising, given the ever-rising attacks.
The second quarter of 2022 ended with over 51 million reports of data breaches. All these latest statistics indicate that cybercrime will be with us for a long time.
However, hackers have embraced a new strategy to materialize their evil intentions. They utilize unrecognized bugs or flaws in a system to break into the network. This technique, known as zero-day attack, has significantly increased in the last year. Zero-day malware increased by 67.2% in the third quarter of 2021, i.e., 3% more than the previous quarter.
You might be celebrating your profits one moment and searching for a vulnerability that incurred you substantial loss the next. That is why it becomes essential to know what these attacks mean. Read the blog to learn what zero-day attacks are, their telltale signs, how they work, and measures to prevent them.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is Zero-Day Attack?
When a hacker or cybercriminal targets a flaw in an application or software unknown to software engineers, the IT team, or vendors, it is known as a zero-day attack. These attacks refer to the threat of a security vulnerability. “Unknown security vulnerability” comprises multiple possibilities. The IT team might not be aware of the issue, or they might have detected it but failed to address it due to insufficient time or because the patch was unavailable before the attack.
The term “zero-day” implies that there is no time between the events, i.e. when developers or vendors discover or identify the vulnerability and hackers exploit it. On the dark web, exploits can be sold for higher prices. These attacks are not bound to a particular system. Hackers target several vulnerabilities to execute their attack, for example, operating systems, office applications, hardware, the Internet of Things (IoT), open source components, watering holes, and web browsers.

Picture this: Your long-awaited vacation is finally here. You have been planning it for a while, and now is the perfect time to hit the road. Like a responsible person, you lock your doors, double-check them, and leave for the airport to spend your next few weeks blissfully. However, a few days later, two burglars decide to tour your neighborhood. They come across your home, and guess what they find? An unlocked back door! You forgot to pay attention to it, but they didn’t. Since you are so cluelessly enjoying your trip, they purloin your valuables before you can take any action. Now, say your house is software or a system, the burglars are hackers, and the unlocked door you didn’t notice is a vulnerability; voila! You are looking at one of the most malicious crimes in the cyber world.
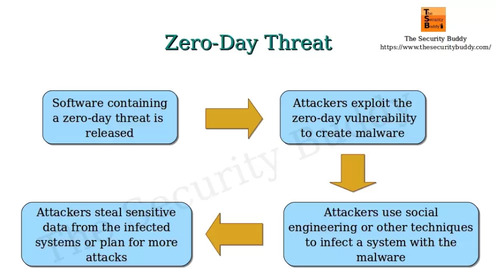
How does Zero-Day Attack Work?
Security experts have divided the workings and execution of a zero-day attack into a few steps:
Step 1: Introduction of vulnerability
Software engineers develop an application or software. They test and scrutinize it by employing various techniques, and the results come out as green. Unknowingly, they release software that contains vulnerable code.
Step 2: Releasing the exploit
A hacker discovers the vulnerability before anyone else can learn about it and create a patch. Now, as the vulnerability is still present, he frames and deploys an exploit code.
Step 3: Discovering the vulnerability
The developer or engineer slowly becomes aware of the vulnerability. However, he identifies a threat, but there is no patch available for it yet.
Step 4: Disclosing a vulnerability
Security researchers or software engineers reveal the vulnerability to the public, informing them of its existence.
Step 6: Introducing the security patch
Developers create a patch for the vulnerability and release it publicly. The time to develop a patch varies depending on the matter’s complexity.
Step 7: Successfully deploying the security patch
The last step is the installation of the security patch. However, it takes time to deploy the security patch on some systems. Therefore, you must enable automated software updates to receive notifications in a timely manner.
Zero-Day Attack Examples
Zero-day attacks are not new in the cyber world. They have been there for a long time. Some of the recent examples of these attacks are:
Chrome Vulnerability
In 2021, Google Chrome became a victim of a zero-day exploit, which caused them to issue an update. The web browser’s V8 JavaScript engine had a bug that led to the vulnerability.
Kaseya Attack
In order to monitor and manage the infrastructure of Kaseya customers, the REvil ransomware managed to compromise the VSA software. REvil Group used zero-day attacks to transfer malicious updates and compromised lesser than 60 Kaseya customers and 1500 downstream companies.
Zerologon
Microsoft came up with a security update in 2011. Researchers at Secure detected a patch for a vulnerability in the Netlogon protocol (CVE-2020-1472) but did not publish any details. Due to the initial lack of attention, it later became one of the highest-scoring security exploits in CVSS (Common Vulnerability Scoring System).
Internet Explorer
Internet Explorer became a victim of a cyber attack due to the way its scripting engine managed the objects in memory (CVE-2020-0674). It severely affected the 9-11 versions.
Microsoft RCE
In 2020, Microsoft discovered zero-day attacks that exploited two vulnerabilities. They had an impact on all supported versions of Windows. The attackers targeted RCE (Remote Code Execution) vulnerabilities.
What is Zero-Day Vulnerability Detection?
You cannot identify zero-day attacks using a traditional signature-based anti-malware or antivirus system. However, here are a few prompts to locate any suspicious activity that might entail an upcoming exploit in your organization:
Patch Management
Although this technique does not detect zero-day attacks, it will help reduce them in your new software versions. Deploying software patches instantly on the most recent applications will limit or eliminate the risk of exposure.
Input Validation and Sanitization
Input validation assists in the inherent issues in vulnerability scanning and patch development. Security experts operate flexible and adaptable input validation and sanitization processes to respond to new threats until they receive the patch.
Zero Day Initiative
The zero-day initiative is a program to appreciate and reward the researchers for detecting and disclosing the vulnerability timely; instead of giving critical information in the black market. The program aims to create a large community of security researchers who can identify and deter vulnerabilities before hackers do and alert the public.
What Losses do Organizations Suffer from Zero-Day Attack?
No organization is immune to cyber attacks unless they incorporate cybersecurity practices. A zero-day exploit is one of the severest malware threats, as no one knows about it besides the hacker. They can expose an organization to several adverse events and cause significant loss. For instance:
- Companies can lose critical, sensitive, or private data
- Hackers often target corporations to steal money
- Affect the production activities and public reputation
- Attackers gain unauthorized control or access to your network, system, server, or website
How to Prevent a Zero-Day Attack?
Zero-day attacks are challenging by nature and cannot be defended in most cases. Many vendors or organizations take immediate measures to develop a patch or attack window to safeguard their customers when there is a 0-day attack. The issue arises when there is a long gap between the announcement of the attack and the delivery of a patch. It becomes risky to rely on one process, especially when it does not guarantee a stark solution. A 0-day attack is a multi-stage process. Although you cannot steer clear of it, you certainly can reduce the chances of exposing your firm by taking preventive steps:
Incorporate SIEM into your security
Security Information and Event Management (SIEM) offers centralized visibility to detect, investigate, and respond to threats in real-time. It evaluates the 0-day attack indicators and attackers using predefined correlation rules and cyber threat intelligence. If any activity or user is found to be suspicious, SIEM tags it as attacker and suspicious. This way, IT managers get hold of the data from the dashboard, reports, and alerts.
Use Firewalls in the System
Firewalls serve as an effective barrier against viruses and other threats. You can integrate them into your systems. It will review and inspect incoming and outgoing web traffic. As a result, your IT team can take adequate actions in time to prevent potential attacks.
Employ DMARC
Cybercriminals frequently use compromised machines to deliver malware. If you have a previously hacked system, isolate and disconnect it from the network. Cybercriminals frequently use compromised machines to deliver malware. If you have a previously hacked system, isolate and disconnect it from the network. Use DMARC in your networks to ensure that no maliciously linked emails enter your network.
Threatcop has a product called TDMARC, which makes it incredibly simple to implement, configure, and monitor email authentication protocols. This helps to stop fraudulent or unauthenticated emails from getting to the intended recipient’s inbox.
Inspect the CPU Level
Hackers usually utilize ROPs (Return Oriented Programs) to go through the defenses incorporated into the CPU. CPU inspection enables you to locate any suspicious bypasses or attempts to overcome space protection and code signing. It also aids in preventing malicious code from being downloaded or executed in the system.
Employee Awareness
No amount of security measures will be effective if your employees do not understand how to use them. It is optimal to hold employee security awareness training to acquire the required knowledge and skills. It will undoubtedly benefit you and your organization in the long run. Threatcop Security Awareness Training is a comprehensive awareness training suite.
Final Thoughts: Zero Day Attack
As technology advances, zero-day attacks will only increase. Unfortunately, you cannot predict or get a quick fix for them. However, it does not mean you cannot be well-prepared when hackers target you. You can use previous data breaches or malicious attacks to analyze network activity. Otherwise, you may be fortunate to detect an indicator for the breach but remain unaware of how it got into your network parameters. Moreover, you can take assistance from professional agencies that strive to provide optimal and exceptional security solutions against various cybercrimes.
How can Threatcop help your organization?
Zero-day attacks are nearly impossible to detect. But, you can reduce exposing your business to these attacks by eliminating the one thing that stays common in almost every cyber attack; Human Error. Whether your firm is small or large, a small mistake by your employee can be a disaster for your organization.
Threatcop provides practical approaches for shielding your business from unknown threats. Threatcop’s main motive is to increase the awareness rate. We offer tons of packages and solutions to ensure your digital safety. We offer multiple products for different purposes, but the motive is one, human error.
Threatcop’s three cutting-edge security products,
- TSAT (Threatcop Security Awareness Training)
- TDMARC (Threatcop DMARC)
- TPIR (Threatcop Phishing Incident Response)
FAQ: Zero-Day Attack
The name of these attacks suggests how they work. Software engineers or IT teams have no time to fix the vulnerability as the hacker exploits the flaw before they know about it.
A zero-day attack occurs when a hacker exploits an unknown vulnerability by releasing malware in an application or software before its discovery.
At its core, a zero-day vulnerability is a fault. It is an undiscovered exploit that can reveal a weakness in hardware or software and cause complex issues before anyone notices anything is wrong.
If you own a company, cyber attacks can knock on your door anytime. However, you can design and implement novel and strategic networks, systems, and management processes to prevent, obstruct, identify, and revert to zero-day vulnerabilities.
Hackers usually target high-profile firms, organizations, government or public institutions, senior employees of corporations, hardware devices, firmware, several home users, etc., to carry out their malicious activity.
