Whenever we discuss cyber attacks, there is one thing that is always left out of the resolution measures, and that is human vigilance. Most organizations around the globe invest a huge amount of money in employing tools to secure their devices. However, they place less emphasis on humans as the first line of defense. In this blog, we are going to discuss the aspects of human defense and dive into the benefits and purpose of security awareness training for employees within the organization.
The increasing number of cybercrimes around the world and the majority proportion of attacks occurring due to the negligence of humans. That’s why organizations are shifting their focus to security awareness training for employees. The purpose of security awareness training is to educate employees about cyber attack vectors and how to defend against them.
According to the IBM Security Report, 95% of cyber attacks occur due to human error. And the average cost of these attacks is $3.3 million.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is Security Awareness Training?
Security awareness training is a set of techniques and strategies that are taught by IT departments and cybersecurity professionals to mitigate and prevent cyber attacks. The training is provided to educate employees so that they can become cyber vigilant. The awareness tool conducts attack simulations and evaluates employees, further educating and training them.
The training will make employees capable of defending themselves against cyber attacks. Effective and good security awareness training focuses on protecting an organization by incorporating practices and policies by identifying possible threats and preventing them.

Purpose and Benefit of Security Awareness Training
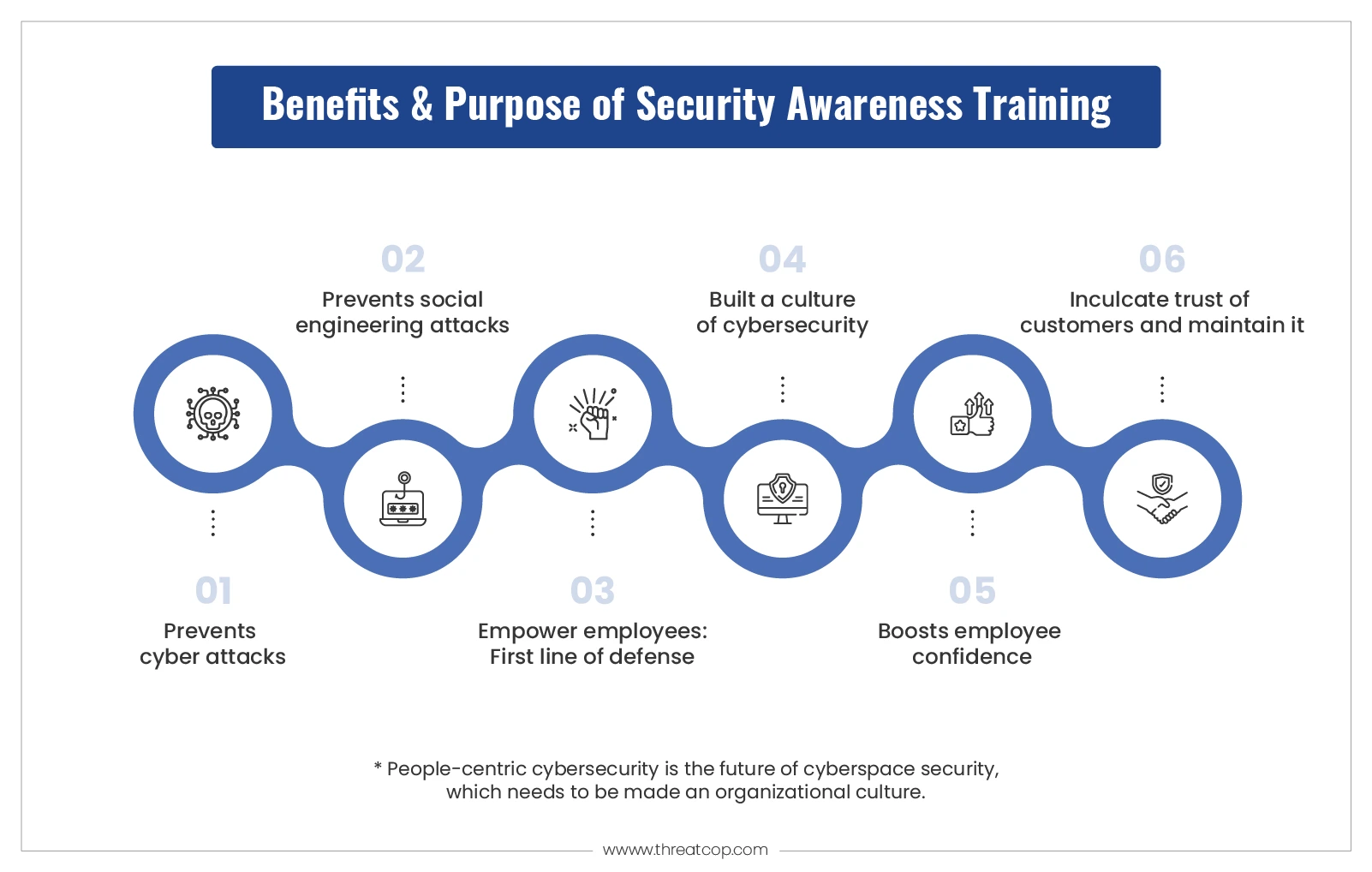
The main purpose of cybersecurity awareness training for employees is to make them aware of cyber attacks and make them vigilant. On a broad level, there are some key purposes of cybersecurity awareness training. You must be wondering what the exact purpose of security training is. Below are listed major benefits and purposes of cybersecurity awareness training.
Empower Employees: First Line of Defense
Organizations worldwide have several employees that carry out operational activities. These employees are working on multiple devices that are part of the organization’s cyber infrastructure. These employees are generally non – technical and don’t have much knowledge about computer security. That’s why most cybercriminals target humans as it is easier to manipulate them than to penetrate devices.
In other words, devices on the network are protected using multiple security mechanisms such as firewalls, tools, etc. However, the systems for employees’ accessibility has become a vulnerability for those devices. This is because, nowadays, cybercriminals manipulate and lure employees into revealing credentials for accessing their devices.
Among all the vectors of cyber attack, the concept of social engineering is the most prevalent and widely used method of attack. Threat actors use social engineering tactics to manipulate and lure employees to get access to private and confidential information.
According to an article from Forbes, 98% of all cyber attacks are based on social engineering tactics.
Prevents Social Engineering Attacks
Social engineering is a categorical attack vector that is mainly used to carry out phishing attacks. The concept of social engineering is to manipulate employees and lure them into revealing credentials or sensitive information. Social engineering attacks are the leading cause of major cyber attacks around the world.
One can easily understand that employees are being tricked into revealing sensitive information. It happens because they are not aware of multiple attack vectors and manipulation techniques used by cybercriminals. To prevent the occurrence of cybercrime, every organization must train their employees. The training makes them more vigilant and aware of how to defend and protect themselves from cyber attacks.
Build a Culture of Cybersecurity
The activity of inculcating cybersecurity as a culture in the workplace means making every employee vigilant and aware. It involves developing a cyber secure workplace by making the employees aware of cybersecurity and threat vectors. The culture of cybersecurity will ensure the values of security in the operations and activities of companies. Culture helps in increasing situational awareness by inducing beliefs, attitudes, knowledge, perceptions, norms, etc.
The development of cybersecurity culture depends on practices and procedures of organizational activities that align with security provisions and techniques. The cybersecurity work culture will not only prevent cyber attacks but also ensure encouragement among employees to make thoughtful decisions.
The essence of cybersecurity in organizations is cyber resilience in the work culture and environment. It is extremely difficult to achieve such a level of resiliency, and that’s why organizations are employing third-party vendors or tools to incorporate the needed mechanism.
The major challenge is that most of the employees are still far behind from being completely aware of the practices. Even the basic practices such as ‘don’t share credentials’ are not followed properly. A healthy cyber environment can be created by using some security practices. These practices should be prioritized and enforced through strict and standard security policies.
They must also be knowledgeable about several cyber attacks that occurred as a result of not following cybersecurity guidelines. The organization should follow three mainstream principles to build a cyber-resilient work culture.
These principles are listed below.
- Cyber resilience should be administered in a top-to-bottom hierarchy.
- Cyber resilience should be incorporated into the business model of the organization.
- Cyber resilience is becoming a driving force for business outcomes as it saves financial loss and increases organization’s reputation.
To mark Cybersecurity Awareness Month, Threatcop collaborated with 31 respected CISOs and CTOs from prominent organizations. Together, we’re working towards a safer digital future.
Explore Here: 31 Cybersecurity Awareness Ideas from Security Leaders
Inculcate Trust of Customers and Maintain It
The increasing rates of cybercrime are a major concern for organizations and their customers. The cybercriminals try to manipulate customers to gain access to their data. Recently, OCBC Bank in Singapore was hit by a series of SMS phishing attacks in which around 790 customers lost $13.7 million.
So, organizations need to incorporate some policies and strategies to sustain the trust of their customers. These strategies are mainly based on a cybersecurity framework that will strengthen the cyber infrastructure of the organization.
Such a level of effort and policies will instill trust in the customers, which will continue to benefit the organization. On the other hand, cyber attacks like data breaches and ransomware attacks will break the customer’s trust and incur a financial loss to them.
Boosts Employee Confidence
The primary objective of cybersecurity awareness training for employees is to equip and familiarize them with the knowledge to defend against cyber threats. Employees who are aware of how to defend against cyber attacks are better able to make smart security decisions and protect themselves as well as the organization.
Overall, having excellent cybersecurity awareness training induces a sense of intellect in employees. The training makes employees knowledgeable, which in turn boosts their confidence. The training and proper learning management systems (LMS) increase the employees’ confidence.
Prevent Cyber Attacks
According to a news article by Gartner, on average, 5.6% of the IT budget is spent on cybersecurity and IT risks in the organization.
Every organization needs to understand the importance of the cybersecurity framework. From the above stats, you can easily understand the obvious cause of cyber attacks. Many organizations lack enough investment to create a robust cybersecurity environment. Most of the investment in the organization goes into the development of cyber infrastructure and not employee awareness.
Organizations need to train their employees with cybersecurity awareness so that they can become a strong line of defense against cyber attacks. Knowing about various kinds of cyber attacks and their attack vectors is an essential ingredient for prevention.
Importance of Information Security Awareness Training
Security awareness training is the best mechanism to start tackling cyber threats. The training provides the knowledge and vigilance to recognize and respond to suspicious threats. This will mitigate and resolve the risk along with developing the cyber security work culture. The importance of security awareness training for organizations is listed below:
- It changes and shifts employees’ mindsets from negligence to cyber awareness.
- Improves an organization’s capabilities and resilience against cyber threats.
- Improve the result of the organization’s security audits and regulatory compliance.
- Mitigate cyber threats and reduce human error.
Confidentiality – Integrity – Availability is the Goal
A good cybersecurity infrastructure in the organization ensures the prevention of cyber attacks and data breaches. Such cyber infrastructure is developed by empowering employees to become capable of preventing cyber attacks. Cybersecurity awareness training is an essential and prominent component of a robust cybersecurity framework.
‘Availability’ is the first goal of an organization’s cybersecurity infrastructure. The strong cybersecurity framework makes sure that digital infrastructure is available and operable without disruption. The next goal is ‘Integrity’, which ensures all the employees and customers of the organization are aligned. The third goal is ‘Confidentiality’, which must be ensured while handling such large amounts of data and information.
Security is a big problem for organizations. The ongoing cyber threats have continued to incur financial damage and data loss to organizations. However, cybersecurity awareness training is still a big challenge for organizations because most of them don’t know the exact mechanism of what training to deliver, who to train, and how to train.

Threatcop Security Awareness Training (TSAT) Tool
We have already gone through multiple perspectives to comprehend the importance of security awareness tools in the organization. Organizations often explore various mechanisms to make sure their employees are well-trained. Threatcop is the best simulation and security awareness tool in the market.
TSAT provides a complete learning management system for security awareness training for employees. The tool provides a platform for creating attack templates that allow the trainer to make a customized attack. This tool is used to simulate dummy attacks on the employees to give them a real-time experience of cyber attacks. This tool provides a complete cybersecurity knowledge base and defense learning for employees.
